![]() For background, you should at least skim-read the paper Transient Astronomy with ACP Scheduler (PDF) Section 7 Digital Signature Features.
For background, you should at least skim-read the paper Transient Astronomy with ACP Scheduler (PDF) Section 7 Digital Signature Features.
The VOEvent Receiver can recognize and check digital signatures that may appear on incoming VOEvent messages. The system for this is described in the IVOA Note A Proposal for Digital Signatures in VOEvent Messages. In addition, the Alerter can digitally sign its outgoing messages. Digital signatures can be used to verify the authenticity of a VOEvent message. This feature requires you to have the GnuPG security software installed on your computer. It also requires you to generate a key for yourself, which is used to sign the outgoing messages from the Alerter. Finally, any incoming messages with signatures can only be validated if you have the public key of the Author of the incoming message.
It is recommended that you use the well-known and portable version 1.4.9 of GnuPG. However, if you already have V2.x installed, and are familiar with it, that's OK. This installation guide is brief, it's beyond the scope of this document to explain how to use the command line, add things to your PATH, etc. If you need help contact DC-3 Dreams and we can help with this. The GNU Privacy Handbook document that comes with GnuPG is invaluable, as is the web page GnuPG Command Reference.
> gpg --gen-key
gpg (GnuPG) 1.4.8; Copyright (C) 2007 Free Software Foundation, Inc.
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law.
Please select what kind of key you want:
(1) DSA and Elgamal (default)
(2) DSA (sign only)
(5) RSA (sign only)
Your selection? 1
DSA keypair will have 1024 bits.
ELG-E keys may be between 1024 and 4096 bits long.
What keysize do you want? (2048)
Requested keysize is 2048 bits
Please specify how long the key should be valid.
0 = key does not expire
n = key expires in n days
nw = key expires in n weeks
nm = key expires in n months
ny = key expires in n years
Key is valid for? (0) 0
Key does not expire at all
Is this correct? (y/N) y
You need a user ID to identify your key; the software constructs the user ID
from the Real Name, Comment and Email Address in this form:
"Heinrich Heine (Der Dichter) "
Real name: ivo://com.dc3/abcd
Email address:
Comment:
You selected this USER-ID:
"ivo://com.dc3/abcd"
Change (N)ame, (C)omment, (E)mail or (O)kay/(Q)uit? O
You need a Passphrase to protect your secret key.
[the passphrase is requested twice here and erased from the shell display]
We need to generate a lot of random bytes. It is a good idea to perform
some other action (type on the keyboard, move the mouse, utilize the
disks) during the prime generation; this gives the random number
generator a better chance to gain enough entropy.
++++++++++...++++++++++++++++++++++++++++++++++++++++++++++++++.++++++++++++++++++++++++++++++++++++
++++..+++++..++++++++++++++++++++.++++++++++>+++++.<+++++................+++++
We need to generate a lot of random bytes. It is a good idea to perform
some other action (type on the keyboard, move the mouse, utilize the
disks) during the prime generation; this gives the random number
generator a better chance to gain enough entropy.
++++++++++++++++++++++++++++++++++++++++.++++++++++.+++++..++++++++++++++++++++++++++++++++++++++++.
++++++++++++++++++++.+++++.+++++..++++++++++....++++++++++>.+++++.+++++>+++++>+++++..............<++
+++...>+++++<.+++++......+++++^^^^
gpg: key FE9654C5 marked as ultimately trusted
public and secret key created and signed.
gpg: checking the trustdb
gpg: 3 marginal(s) needed, 1 complete(s) needed, PGP trust model
gpg: depth: 0 valid: 4 signed: 0 trust: 0-, 0q, 0n, 0m, 0f, 4u
pub 1024D/FE9654C5 2009-03-17
Key fingerprint = 9855 AEB7 06E8 E5ED B840 47F6 28AD 96B0 FE96 54C5
uid ivo://com.dc3/abcd
sub 2048g/8D2598CD 2009-03-17
>
> gpg --list-keys C:/Documents and Settings/Some Name/Application Data/gnupg\pubring.gpg ---------------------------------------------------------------------------- pub 1024D/FE9654C5 2009-03-17 uid ivo://com.dc3/abcd sub 2048g/8D2598CD 2009-03-17
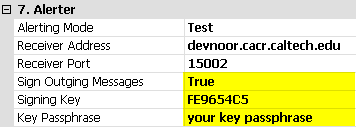 Note the hex public Key-ID (FE9654C5 in the example above, 'pub').
Note the hex public Key-ID (FE9654C5 in the example above, 'pub').After doing this, the Alerter will send all alert VOEvent messages signed by you (the Author IVORN).
In order to validate an incoming VOEvent, you must have the public key of the Author of the incoming VOEvent message. When the receiver detects a digital signature on an incoming message, it will attempt to validate the signature. If it succeeds, the filter will get the User-ID of the signer in the //signer named argument (see Command Line in Customizing the Event Filter). In order to succeed, you must have installed the public key of the Author, and the message must not have been altered in any way during transmission from the Author to you.
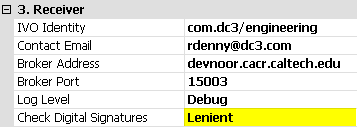 Note that the receiver has three modes of signature validation. See the image on the right. Disabled means that no signature checks are made at all. Lenient means that any signature that appears in a message will be checked, but the message will always be passed to the filter. Strict means that the message must have a signature, and it must validate, otherwise the message will be discarded and not sent to the filter.
Note that the receiver has three modes of signature validation. See the image on the right. Disabled means that no signature checks are made at all. Lenient means that any signature that appears in a message will be checked, but the message will always be passed to the filter. Strict means that the message must have a signature, and it must validate, otherwise the message will be discarded and not sent to the filter.
If the filter gets the //signer parameter and it's non-blank, it means that the message has a signature and it is valid. At this point the filter can check the //signer against the Author IVORN of the message. If it matches, then the filter knows it has a completely valid message. If the //signer is non-blank but its value doesn't match the Author IVORN, it means that someone other than the Author signed the message, and the filter can decide what to do with it. If there is no //signer, then either there is no signature, or there is a signature, the mode is Lenient, and the signature did not validate. Again the filter can decide what to do with such messages.
![]() The receiver does not check the Author IVORN against the User-ID of the public key used to validate the signature. It is the responsibility of the filter to do this!
The receiver does not check the Author IVORN against the User-ID of the public key used to validate the signature. It is the responsibility of the filter to do this!
In order for anyone else to validate the signatures applied by the Alerter (your outgoing VOEvent messages) they must have a copy of your public key. This is easy to make using GPG:
> gpg --output MyVOeventPubKey.asc --armor --export ivo://com.dc3/abcd
The --armor option creates an "ASCII-armored" file that can be easily mailed in a plain-text email. Here's what the contents of an ASCII-armored file looks like:
-----BEGIN PGP PUBLIC KEY BLOCK----- Version: GnuPG v1.4.8 (MingW32) mQGiBEnAXrIRBACF41Bq+dc2jsCGDjE8mR7YGqDiOXNnGWu1I3kXo62USYdHUnr9 3tXgktKeiZtTnC6Le8URDomflrAxgKXVsCRBerEC3PrV7NZxwQk8MFi069zDwFeR 0w2I+hEHNpv/rvWmv18awswF4o2vF8TN6goLkr272YL+GA5PL39SjDwQLwCgiJnk xxIQ7sE5sk6UcgelH//gJKcD/3G0h+wMs8g5nbchiKJOokB3R8gQMzVCLOdqguzV P/+KXMf/PbG4b/sK6p+NbbDmqlzZinohX45185A9INhiffCPKVrBBKCmKqAQHcZx /SyzqQtNl8kcZkZEX/8jSOulpTPf1q09eDmrvLHBgGmIpkj9iciHWe3Ht02LpRQo 1ZMpA/9UmjtvpBW6YNlOnOuGUDAKEQBGiJM+YiH50SYMgaUs8xDylu9BAGKMOXgg Gey4NsUBgu9aibGQkD/GgX7GWtuajy30ArRxr2oOeih5eaYWwvCWs3/BqNvrPHGa ZiIziJAu3mcC1d9uyadvFgC10LlSMLv1Pxq4QsiwkhLnZzLC1rQSaXZvOi8vY29t LmRjMy9hYmNkiGAEExECACAFAknAXrICGwMGCwkIBwMCBBUCCAMEFgIDAQIeAQIX gAAKCRAf8jYAqUZ9JO4bAJ9PQO9Pm2woRloHVMdqBJ0DxvzMvwCfRdnH5L1kjhNO dHLYvxliCVGkHBm5Ag0EScBeshAIAMhC9L0hBb3edbWT3gJmy37D49BI0RCnESiC b0d5Se43gi/voK2dYNlW+HKDf3wkL3pzSRpbxApW3zKb8g4Qd2rofJscxCNEJyjy nBuPVzdsupjsc6iLev4dTrNnxGJqBUebXNvPV0j1LCospc7TO83Ci6XxdG4/KFM8 pI7VU2Gs+MllhmKaof2AyvD+1GN02cvGWpwzvThEmQ8yFi5Xcul2JG538ogwyVeK FBTAE7sPONzsDroRRv5xBMpqYuJTIVAcuD9pwr8sGH4JqQ/mATfzXGTNI8/thSUq oMJvs5V7oTx19d9XrpRAbC691tMVkmUD461M8Y0W5l2GAL4B5QsAAwUIAK1N3HZD 5IV75twlqKW8MWqhjpXL3WtNkZQ4IgiebLx64jQDalCQDWPIaP3Wv8boDur3BVQe eF/8eCQRhS0AwYQ1PVMTT7vKZ91NO4c4hg/zlZOgNpK4uu2h0XZnQoGCLct52hcK 85BQbHkWS5ty3m0mXs7a6yfvdTgrTfqe+jxId8HsLXU3mi8hfSjIT8f5r88MDRqg vuN3ExWOW7HhaCtSqvYdQ8MfgCyT8mcPwU5CDnV3auuizNnPDVYZm7aTx+eW2XfW ABj9LIl+3mH6VeBSFIgo27Gqe+9FTmBk+7KI8JjC7WaTyLmp7L6GfRuo5aCgjvUP vE8rjRpo5p9rdFKISQQYEQIACQUCScBesgIbDAAKCRAf8jYAqUZ9JIOpAJ4kjfpX mmanfI0QTiprHB7ve54AuACbBfGEbJcLu+ADRcrSoOCKduswdcc= =+lRB -----END PGP PUBLIC KEY BLOCK-----
Send this to your intended recipient(s).
As described in the previous section, you must have the public key of a VOEvent's Author in your keyring in order for the receiver to validate the signature of signed messages from that Author. Assuming they exported their public key as described in the preceding section, you simply import it into your keyring like this:
> gpg --import SomeAuthorsPubKey.asc
Once it is imported, take a look at it with the gpg --list-keys command and make sure it is what you expected from that Author.